SIEM (Security Information and Event Management) is a mandatory tool for Security Operation Center which is used to collect events from all data sources. If the SIEM is performing little more operations like automated response for the security alerts, then we can reduce our analyst counts and save time by looking into how to enhance the security of the organization.
Azure Sentinel is a SIEM and Security Orchestration and Automated Response (SOAR) system in Microsoft’s public cloud platform.It can combine alert detection, threat visibility, proactive hunting, and threat response into a single solution. It gathers data from several sources, performs data correlation, and displays the processed data in a single dashboard. Security threats and incidents can be collected, detected, investigated, and responded by using Azure Sentinel.
Azure Sentinel includes Azure Logic Apps and Log Analytics, enhancing its capabilities. It also has advanced built in machine learning capabilities, which can spot threat actors and suspicious activities, greatly assisting security analysts in their analysis of their environment. Azure Sentinel is simple to set up in both single and multi-tenant environments.
Also Read: Most Common Malware Obfuscation Techniques
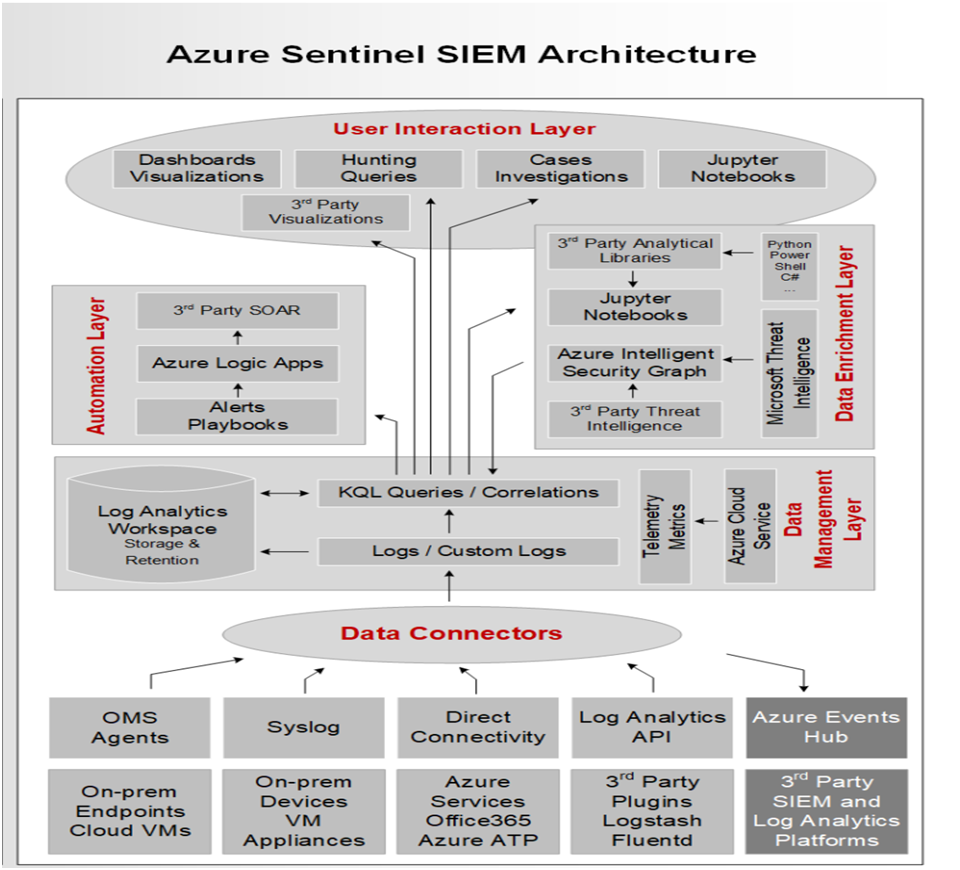
Azure Sentinel Architecture:
Azure sentinel can further identify by understanding its core capabilities.
Collect Data:
Azure Sentinel can gather data on all users, devices, applications, and infrastructure on-premises and in multiple cloud environments. It has an easy-to-use interface for connecting to security sources right out of the box. For Microsoft products, there are various connectors that offer real-time integration. It also has built-in third-party product and service interfaces (non-Microsoft Solutions). Apart from that, Azure Sentinel can connect to the relevant data sources via Common Event Format (CEF), Syslog, or REST-API.Azure Sentinel supports both Fluentd and LogStash to connect and collect data and logs.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
- The appliances that can use the API to connect to Okta SSO, Orca Security, Qualys VM, Citrix Analytics, Barracuda CloudGen Firewall, Perimeter 81 Logs, Proofpoint TAP, and others.
- Azure Active Directory, Azure Activity, Azure DDoS Protection, Azure AD Identity Protection, Azure Firewall, Azure Security Center, Azure Web Application Firewall, Office 365, Microsoft Defender for Identity, Amazon Web Services – CloudTrail, Cloud App Security, and other Microsoft solutions are among the services that can be connected directly via out-of-the-box integration.
- Any other data source can also be connected to Azure Sentinel using an agent. The Syslog protocol can be used for this, and it allows for real-time log streaming. The Log Analytics Agent, which is part of the Azure Sentinel Agent function. Its purpose is to convert CEF-formatted logs into a Log Analytics-compatible format. Linux servers, DNS servers, Azure Stack VMs, and DLP systems are examples of external solutions supported by Azure Sentinel via agents.
- Threat Intelligence Providers (MISP Open Source Threat Intelligence Platform, AnomaliThreatStream, Palo Alto Networks MineMeld, ThreatConnect Platform, ThreatQ Threat Intelligence Platform, etc.). Firewalls, proxies and endpoints supported through CEF (Check Point, F5 ASM, Palo Alto Networks, Zscaler, Cisco ASA, Fortinet, and other CEF-based appliances), and firewalls, proxies and endpoints supported through Syslog (Sophos XG, Symantec Proxy SG, Pulse Connect Secure and other Syslog-based appliances).
Also Read: Latest Cyber Security News – Hacker News !
Detect Threats:
Using analytics and threat intelligence directly from Microsoft, Azure Sentinel can detect threats and reduce false positives. Azure Analytics serves a critical role in correlating alerts with security team-identified issues. It comes with built-in templates for creating threat detection rules and automating threat responses right out of the box. Along from that, Azure Sentinel also allows for the creation of custom rules. The four built-in templates are listed below:
- Microsoft Security Templates- When this template is used, Azure Sentinel incidents will generate a real-time flow of alerts that are generated by other Microsoft security products.
- Fusion Template- By default, this template can only produce one rule and is disabled. It’s based on powerful multistage attack detection logic. It employs scalable machine learning techniques to convert a large number of low-fidelity alerts and events from various products into high-fidelity and actionable incidents.
- Machine Learning Behavioral Analytics Template – Each type of template can only build one rule. These are built on Microsoft’s proprietary Machine Learning Algorithms, and users have no access to the template logic’s underlying workings or the time it takes to run.
- Scheduled Templates- This is the only template that allows users to see the query logic and make adjustments based on the environment’s needs. Scheduled templates are analytics rules that are based on Microsoft’s built-in queries. To develop new rules, these templates can be customized in terms of query logic and scheduling settings.
Also Read: Next Generation SIEM features – Transform your soc with Next-gen SIEM
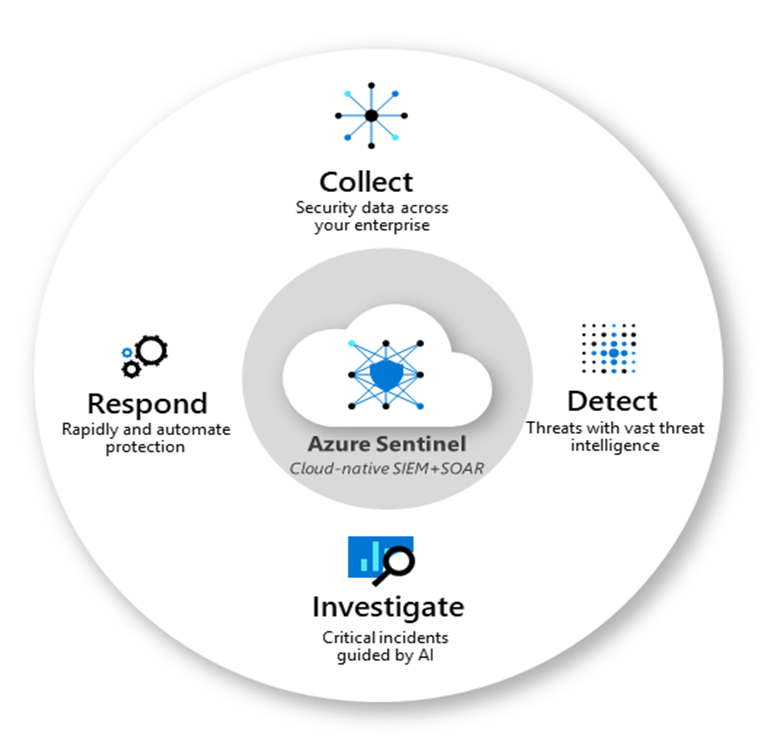
Suspicious Activity Investigation:
Azure Sentinel can investigate and track suspicious behaviors all around the place. Based on the MITRE framework, it helps decrease noise and look for security threats. To detect suspicious activity, use Artificial Intelligence to proactively identify threats before an alert is triggered across the protected assets. The following features are available when using Azure Sentinel for hunting and investigation:
- Create your Bookmarks:Create bookmarks for your findings that you come across during the hunting process so that you can go back and review them later and create an incident for further investigation.
- Automate your investigation with notebooks: Notebooks are similar to playbooks in that they offer a step-by-step guide. That you can use to keep track of the steps involved in a search and rescue operation. These notebooks compile all the processes required in the hunting process into a reusable playbook that can be shared with other team members.
- Built-in Queries: This feature was created by Microsoft and is provided to help you learn about tables and the query language. You may, however, develop new queries or fine-tune old ones to improve your detecting abilities.
- Intelligent Query Language: It is built on top of a query language that gives you the freedom you need to take your hunting capabilities to the next level.
- Query the Stored Data: The data associated with and generated by Azure Sentinel is easily accessible and available in the form of tables.
- Community Connections: Additional queries and data sources can be found in the Azure Sentinel Github community.
Respond:
Azure Sentinel can handle built-in orchestration incidents seamlessly and swiftly, and routine and repetitive activities may be readily automated. It can use playbooks to create easier security orchestration. When an event occurs, it can also create tickets in ServiceNow, Jira, and other systems.
Conclusion:
Here we have gone through what is Sentinel and the main core capabilities of it. In the next blog we will be covering the Components of Azure Sentinel.