The Infinitum IT Cyber Threat Intelligence team successfully monitored one of the key members of the Conti Ransomware group. Security researchers found a connection between Conti ransomware and the recently emerged Karakurt data extortion group, showing that the two gangs are part of the same operation.
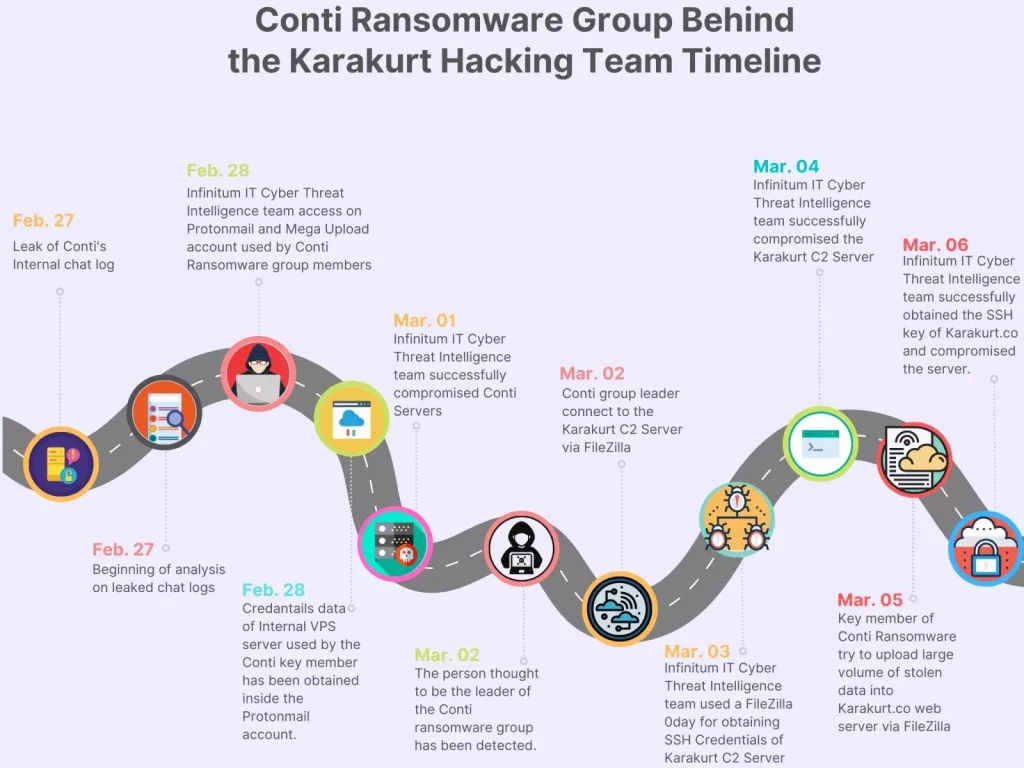
Cybercriminal Operation Timeline:
Infinitum IT Cyber Threat Intelligence team is able to obtain remote access on multiple servers, they are being actively used by members of threat actors as command and control server, storage server that has stolen private data from various victims, and web server that is being used by Karakurt Hacking team.
Threat actors like Ransomware groups used their web pages to share large numbers of exfiltrate data that are being stolen from victims, they are using data to threaten the victim companies to pay the ransom money.
Karakurt is a well-known threat actor group that has launched cyberattacks against several Canadian and US organizations. On December 29, 2021, the Karakurt group claimed on its website that it had struck 11 organizations as part of its “Winter Data Leak Digest.” Of the 11, six were based in Canada. The group claimed to have compromised more than 40 victims between September and November 2021, sharing the stolen files on its name and shame blog website.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Karakurt focuses exclusively on Data Exfiltration, they are not using Ransomware to encrypt victims’ files. The group accomplishes this by first using VPN credentials to access victims’ networks, through phishing attacks against victims.
Internal Infrastructure Used by Conti and Karakurt Group:
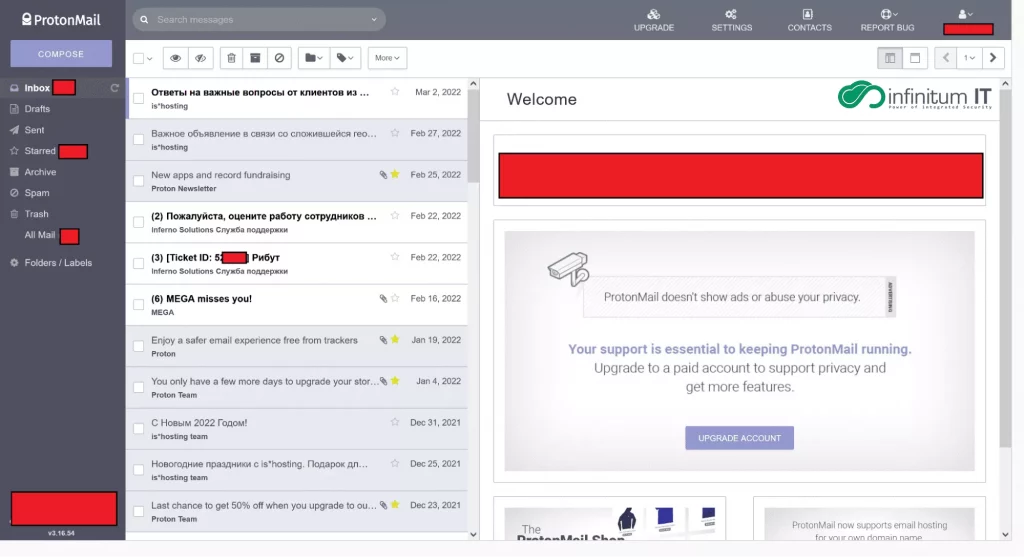
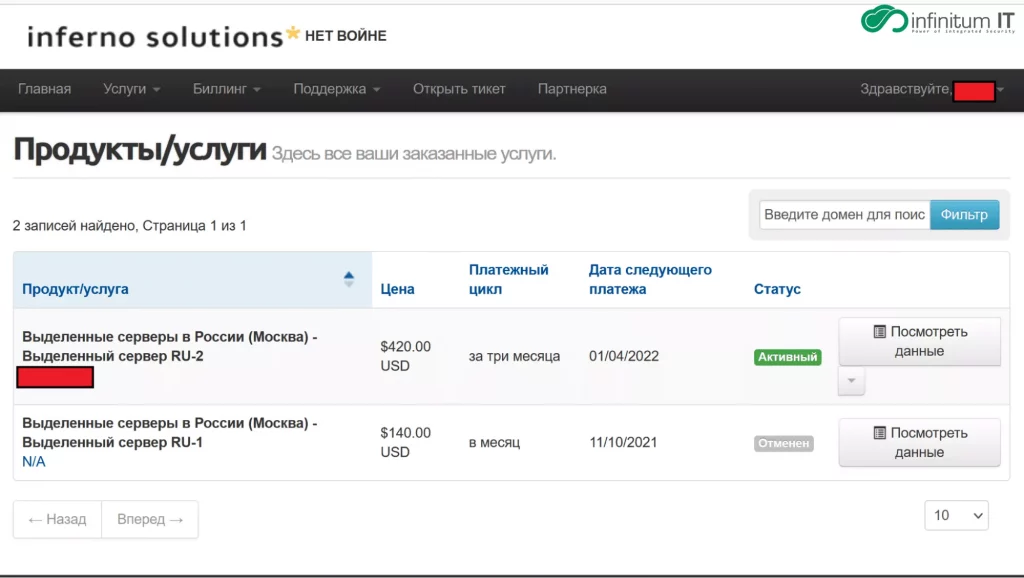
At the beginning of the Conti leak on February 27, 2022 Infinitum IT are able to get inside multiple Protonmail and Mega Upload accounts used by one of the key members of Conti Ransomware group, after further investigation Infinitum IT observed threat actors used multiple Protonmail accounts for OPSEC reasons and able to archive the content of mail traffic and Infinitum IT observed multiple emails coming from Russian VPS Service called Inferno solutions and Infinitum IT gained the remote access on one of the Windows VPS Server that being used data storage system. That has more than 20 TB+ of stolen victim data.
Windows Data Storage Server Used by Conti Ransomware:
Security researchers at Infinitum data storage server that is being used for storing large volumes of stolen data from victims and the usage of Mega Upload account to manage this overall 20TB+ data. Some of the data were old but not published publicly.
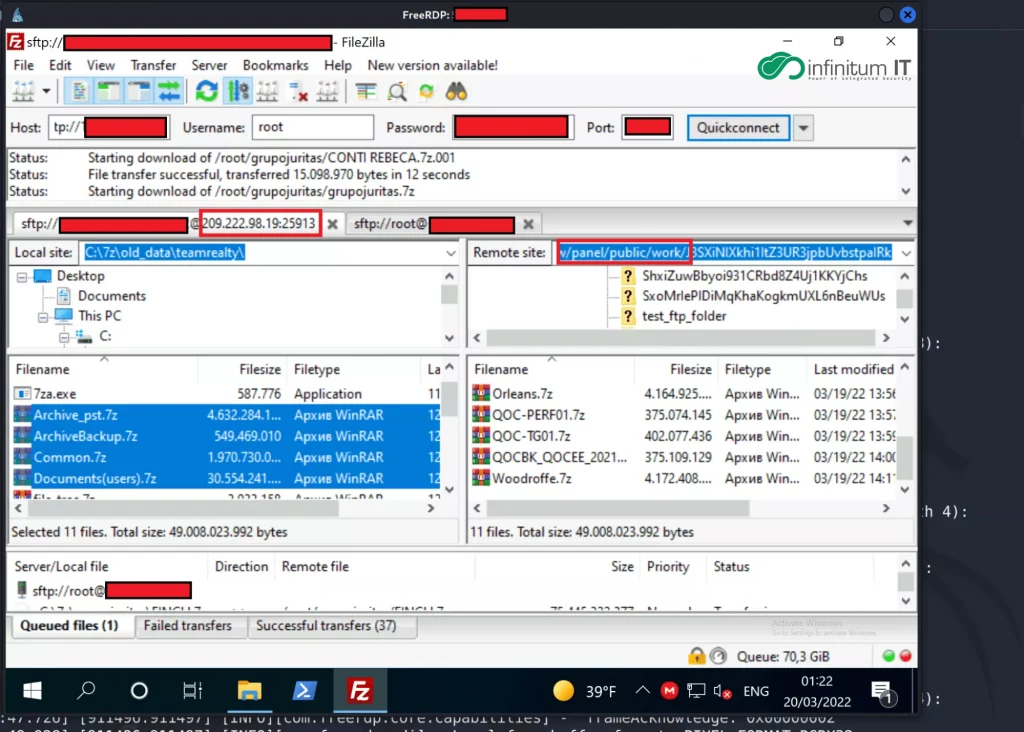
Conti member used FileZilla to connect multiple remote servers, the main purpose is to upload the stolen data to another server for preparing the public release. Take a closer look at the IP address 209[.]222[.]98[.]19 the DNS record shows us, it belongs to the karakurt[.]co blog page which is being used for sharing the stolen files.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
During connection of remote server via FileZilla, Conti members don’t save any Password credentials, but Infinitum IT Cyber Threat Intelligence team successfully obtained the SSH Credentials via a 0day vulnerability affected by FileZilla and used these credentials to get inside the Command and Control Server. The attacker also used an SSH Private key to connect karakurt[.]co blog page, Infinitum IT managed to obtain the private key.
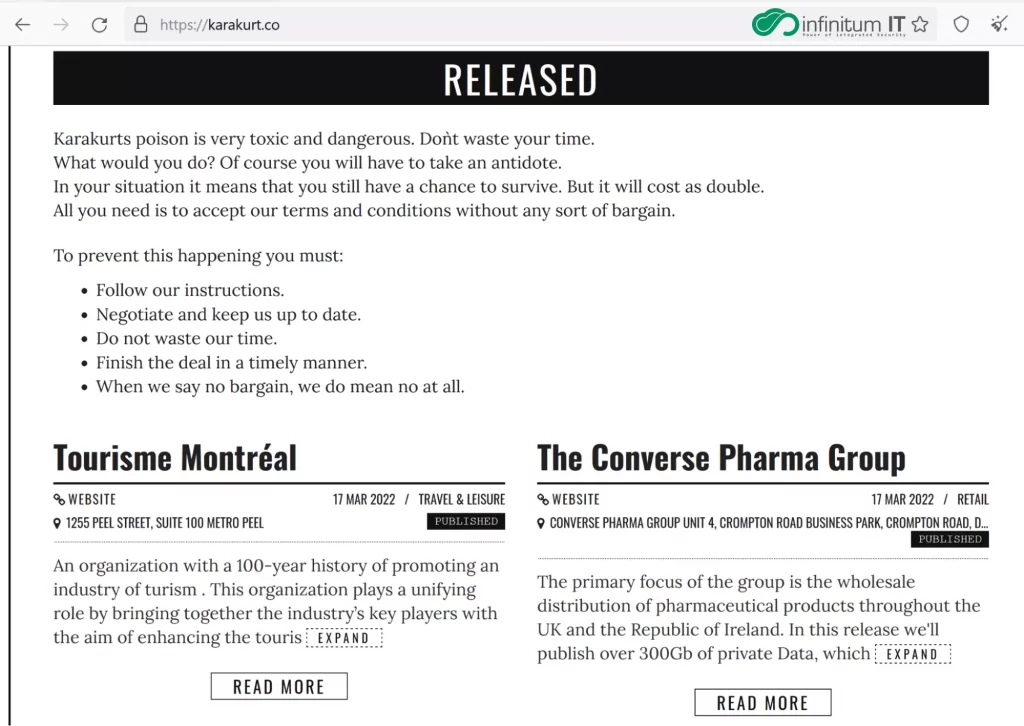
Karakurt Blog Web Server:
Security researchers connected to the Karakurt Blog Web Server saw that all of the stolen data had been categorized by Software that was being developed by Karakurt members. During the analysis, they are able to find an Admin Panel used by Karakurt and Server LOG data. The Admin panel is being used for visualizing and filtering all stolen files.
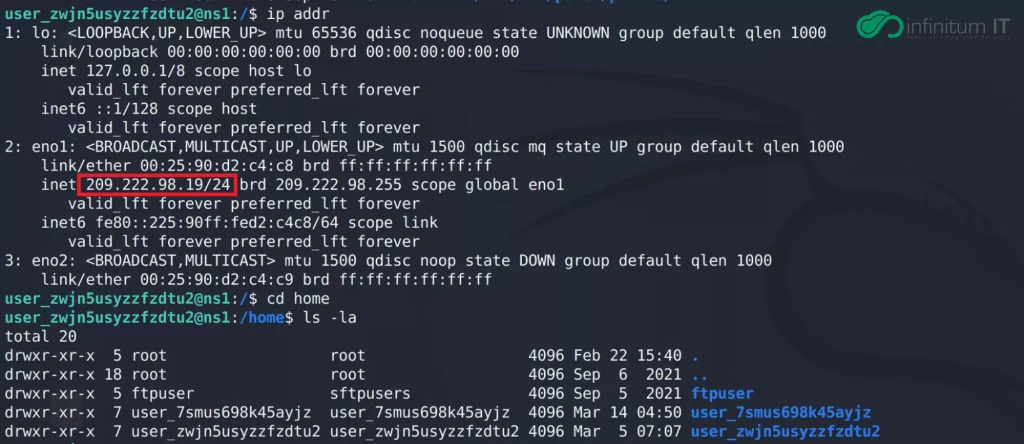
The Infinitum IT Cyber Threat Intelligence team found this server also being used by the TOR network to serve itself on Darknet.
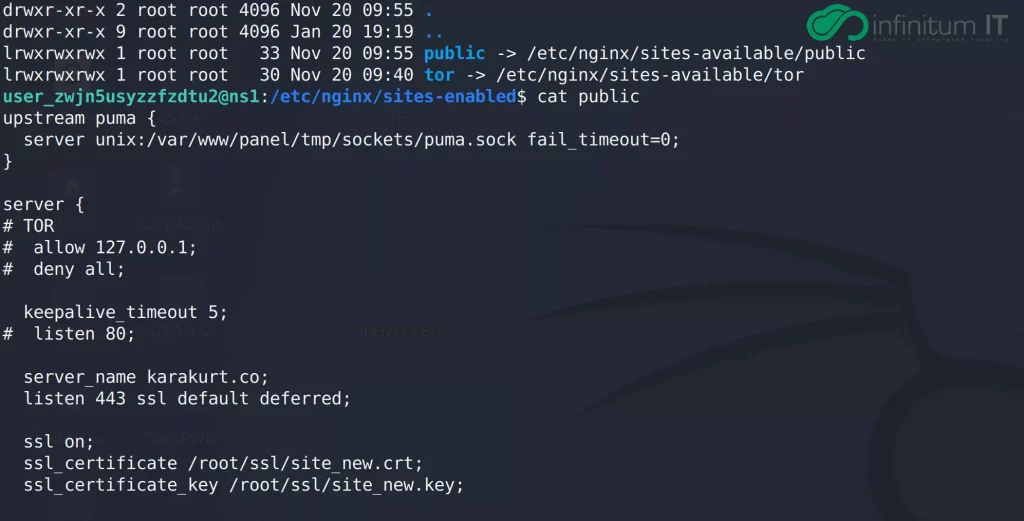
All of the stolen data has been uploaded by multiple Karakurt members on one file called Work,this data then being categorized as public or not public. We can easily see the Karakurt hacker team being more interested in Financial data from victims’ devices.
Also Read: SystemBC Malware Being Used by Various Threat Attackers – Initial access to Indicator of Compromise
All of the stolen data has been uploaded by multiple Karakurt members on one file called Work, this data then being categorized as public or not public. We can easily see the Karakurt hacker team being more interested in Financial data from victims’ devices.
Command and Control Server:
The Infinitum IT Cyber Threat Intelligence team is able to access the Command and Control Server that is being actively used by the Karakurt Hacking team on cyber attack operations. As a summary of the attack chain, researchers observed the use of open source tools like
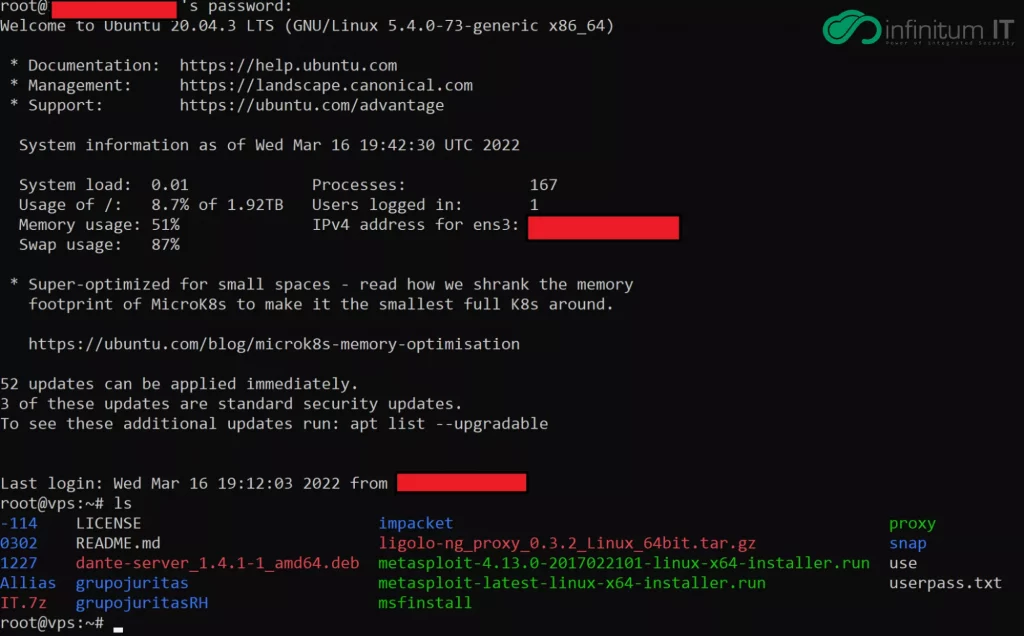
- Ligolo-ng : Getting Initial Access on companies network via Reverse Tunneling, this technique being used for bypassing miss configured Firewall systems.
- Metasploit : Karakurt used Metasploit as C2 server and in post exploitation phase details can be seen on Metasploit log file that was obtained and shared by the Infinitum IT Cyber Threat Intelligence team on IOC part.
- Impacket: After getting Initial Access on the victim company network, Karakurt hacking team use Impacket to perform NTLM relay attacks. This tool mainly used for Lateral Movement
- Danted: Fast script for installing & configuring Danted–Socks5 Proxy Server. That being used for Reverse Tunneling.
Mitigation Against Conti / Karakurt Hacking Team:
- Employ robust and routine user-awareness and training regimens for users of all systems.
- Ensure that a robust crisis management and incident response plan are in place in the event of a high impact intrusion.
- Maintain best practices against malware, such as patching, updating anti-virus software, implementing strict network egress policies, and using application whitelisting where feasible.
- Patch infrastructure to the highest available level, as threat actors are often better able to exploit older systems with existing vulnerabilities.
- Ensure all internet-facing security and remote access appliances are patched to the latest versions.
- Disable RDP on external-facing devices and restrict workstation-to-workstation RDP connections.
- Employ a strong corporate password policy that includes industry standards for password length, complexity, and expiration dates for both human and non-human accounts.
- Use MFA where possible for authenticating corporate accounts to include remote access mechanisms and security tools. Admin accounts should be cross-platform MFA enforced.
- Use admin accounts only for administrative purposes and never to connect to the network or browse the internet.
- Do not store unprotected credentials in files and scripts on shared locations.
- Deploy EDR across the environment, targeting at least 90% coverage of endpoint and workload visibility.
- Encrypt data at rest where possible and protect related keys and technology.
- Hunt for attacker TTPs, including common “living off the land” techniques, to proactively detect and respond to a cyber-attack and mitigate its impact.
Indicators of Compromise:
| Domain | IP |
|---|---|
| karakurt.co | 209.222.98.19 |
| stok-061153.stokermate.com | 104.238.61.153 |
| Onion site | IP |
|---|---|
| lhxxtrqraokn63f3nubhbjrzxkrgduq3qogp3yr424tkpvh3z7n4kcyd[.]onion | 104[.]243.34.214 |
The following table contains the authentication logs of the subject Karakurt servers with IP 209.222.98.19 and 104.238.61.153
| Detected TCP Connections on Karakurt Servers |
|---|
| 45.8.119.60 |
| 212.220.115.145 |
| 5.45.83.32 |
| 31.14.40.64 |
| 95.170.133.54 |
| 1.116.139.11 |
| 45.141.84.126 |
| 185.5.251.35 |
| 49.232.93.149 |
| 61.177.173.17 |
| 80.93.19.227 |
| 139.219.4.103 |
| 61.19.125.2 |
| 159.65.140.76 |
| 23.99.177.202 |
| 109.169.14.109 |
| 104.243.34.214 |
| 37.252.0.143 |
| 46.166.143.114 |
In infinitum IT CTI research on Karakurt / Conti Servers, we are able to identify the use of SOCKS proxy pivoting technique with a open-source tool called Ligolo-ng against multiple victims.
Also Read: Xanpei Virus Infecting Normal Excel Files
The following table contains the Ligolo-ng Agent and Command and Control Server used by Karakurt Hacking Team Members
Ligolo-ng Agent and Command and Control Servers
| Ligolo-ng Agent and Command and Control Servers |
|---|
| 104.194.9.238/download/lig.ext |
| 104.194.9.238:455/download/lig2.ext |
| 104.238.61.153 |
Readers can find the new samples, IOCs, and new versions of this report from github page.
Source/Credits: Infinitum IT CTI research Team



































