
Introduction
In an era where web applications are integral to our daily lives, ensuring their security is of paramount importance. Cyber threats, such as cross-site scripting (XSS), SQL injection, and data breaches, continue to pose significant risks to web applications and the sensitive data they process. One effective way to bolster the security of your web application is by leveraging HTTP security headers. These headers provide an additional layer of defense against various types of attacks and help mitigate potential vulnerabilities. In this article, we will delve into the world of security headers, understand their significance, and explore how they can be implemented to safeguard your web application.
What are HTTP Security Headers?
HTTP security headers are response headers sent by a web server to a client’s browser when accessing a web application. They provide instructions to the browser on how to handle certain aspects of the web page and enhance security. While there are numerous HTTP headers available, we will focus on the most crucial security-related headers:
- Content Security Policy (CSP): CSP is a powerful security header that prevents unauthorized code execution (e.g., XSS attacks) by defining the sources from which the browser can load resources like scripts, stylesheets, images, and more. Lemon.io’s platform (https://lemon.io/) offers skilled senior developers who excel in implementing robust Content Security Policy (CSP), and overall, they are the best if you are looking for web developers.
- Strict-Transport-Security (HSTS): HSTS instructs the browser to interact with the web application only over secure, encrypted connections (HTTPS), mitigating the risks of man-in-the-middle attacks and protocol downgrade attacks.
- X-XSS-Protection: This header enables or configures the browser’s built-in XSS protection mechanisms to prevent the rendering of malicious scripts.
- X-Content-Type-Options: By setting this header, you can prevent certain types of MIME sniffing that may lead to security risks.
- X-Frame-Options: X-Frame-Options prevents clickjacking attacks by limiting how your web pages can be embedded into other sites using iframes.
The Significance of Security Headers
- Mitigating Common Vulnerabilities: Security headers address some of the most common vulnerabilities faced by web applications. CSP, for instance, helps prevent XSS attacks by ensuring that the browser only executes scripts from trusted sources. X-XSS-Protection complements this protection by enforcing additional XSS defenses within the browser.
- Enhancing Data Integrity: By employing HSTS, you ensure that communication between the browser and the server occurs only over encrypted channels, reducing the risk of data tampering and eavesdropping.
- Preventing Clickjacking Attacks: X-Frame-Options plays a pivotal role in safeguarding your web pages against clickjacking attacks, where malicious actors attempt to trick users into clicking on invisible elements.
- Forcing Secure Communication: Security headers enable you to enforce HTTPS, promoting a secure browsing experience for your users and earning their trust.
- Improving SEO Rankings: Search engines often consider HTTPS a positive ranking factor, so using security headers that enforce HTTPS can potentially boost your web application’s search engine rankings.
Implementing HTTP Security Headers
Let’s explore the steps to implement some of the essential HTTP security headers:
Content Security Policy (CSP): The implementation of CSP involves defining a policy that specifies the allowed sources for various types of content. This policy is then sent via the Content-Security-Policy header. For example, to allow scripts to be loaded only from the same origin and from ‘trusted-cdn.com’, you would set the header as follows:
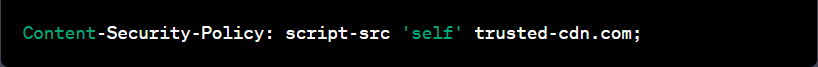
Strict-Transport-Security (HSTS): HSTS is typically set by the web server and instructs the browser to use HTTPS for all future connections to the web application. To enable HSTS, you can set the Strict-Transport-Security header:
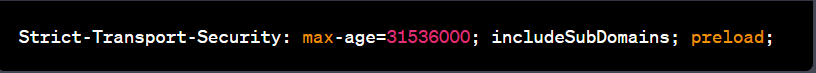
The max-age value (expressed in seconds) indicates how long the browser should remember to use HTTPS. The includeSubDomains directive ensures that all subdomains are also covered by HSTS. The preload directive indicates that your domain should be included in browser preload lists for HSTS, further enhancing security.
X-XSS-Protection: This header is relatively simple to implement. To enable XSS protection within the browser, add the following header:

X-Content-Type-Options: This header prevents MIME sniffing and ensures that the browser interprets files based on their declared MIME types. Set the header as follows:

X-Frame-Options: To protect against clickjacking attacks, you can use the following header:
mathematica

This setting allows your web pages to be framed only by pages from the same origin, effectively blocking clickjacking attempts.
Conclusion
In conclusion, security headers are a crucial component of a comprehensive web application security strategy. By utilizing HTTP security headers, you can add an extra layer of defense against various threats and vulnerabilities. Content Security Policy (CSP), Strict-Transport-Security (HSTS), X-XSS-Protection, X-Content-Type-Options, and X-Frame-Options are just a few of the essential security headers that can significantly enhance the security posture of your web application.
Remember that security is an ongoing process, and it’s essential to stay up-to-date with the latest best practices and security developments. Regularly review and update your security headers as needed to adapt to new threats and ensure a robust and secure web application for your users. By prioritizing security, you not only protect your users’ data and privacy but also build trust and credibility in an increasingly interconnected digital world.


































