In 2021, the people accessing the network are in billion. Customers, vendors, and even remote users will be accessing our network. The lonely hacker who is bored with his daily routine has nothing better to do but try to break into our network. So to find the difference between legitimate and fraudulent connections, there is a need for one best system which should have the capability to handle billions of logs at a time. This is where an Intrusion Detection System and Intrusion Protection System can lend a hand. IDS and IPS pair up to provide network security. When IDS and IPS are combined, we can detect and stop hackers before they gain access to sensitive data on our network. IPS can keep in the inline mode which will act as both IDS & IPS which is called as Intrusion Detection & Prevention System (IDPR). IDS/IPS are both vital in protecting our network. They work together to monitor traffic and report attacks. A good security strategy is to have them work together simultaneously.
What is IDS?
An Intrusion Detection System (IDS) detects and reports on attack attempts in their early stages. Any action that appears to be hazardous is frequently reported to an administrator.
What is IPS?
An intrusion prevention system (IPS) (also often called “intrusion detection and prevention systems” or IPDS) is a technology for detecting, reporting, and even preventing suspected malware.
IDS/IPS Detection Techniques:
Different approaches for detecting suspected intrusions are:
- Pattern matching
- Statistical anomaly detection
- Policy-Based Detection
- Stateful Protocol Analysis Detection
1. Pattern Matching (signature-based Detection):
A signature-based IDS or IPS sensor looks for specific, predefined patterns (signatures) in network traffic. It compares the network traffic to a database of known attacks, and triggers an alarm or prevents communication if a match is found. The signature can be based on a single packet or a sequence of packets. Pattern matching’s major flaw is that it misses new attacks for which the software doesn’t have a specified signature in its database. The effectiveness is reliant on the signature database, which must be kept up to date.
Advantage:
- Very effective at detecting known threats.
Disadvantage:
- They are unable to detect novel attacks.
- There will be more false alarms in the future.
- Every new pattern that is discovered requires reprogramming.
2. Statistical anomaly detection
Anomaly-based or profile-based signatures typically look for network traffic that deviates from what is seen “normally.” It watches for deviations from normal usage patterns. This requires first establishing a baseline profile to determine what the norm is, then monitoring for actions that are outside of those normal parameters. However, the challenge with these systems is eliminating the possibility of improperly classifying abnormal behavior as normal.
There are several different anomaly detection methods, including:
- Metric model
- Neural network
- Machine learning classification
Advantage:
- This enables you to detect novel intrusions or attacks that haven’t yet been identified.
Disadvantage:
- The major flaw in this approach is that it requires you to first define what normal is. If our network is attacked during the learning phase and you fail to recognize it, the anomaly-based IPS systems will interpret the malicious traffic as normal, and no alarm will be triggered the next time the same attack occurs.
- Alerts will be flooded with false positives because odd behavior will be detected as a possible attack even if it isn’t.
- Assumes that intrusions will be accompanied by manifestations that are sufficiently unusual to permit detection.
3. Policy-Based Detection:
The IDS or IPS sensor in policy-based systems is preset based on the network security policy. In a policy-based IDS or IPS, you must create the policies. If traffic is identified outside of the policy, an alarm will be triggered or the traffic will be dropped Policy-based signatures use an algorithm to determine whether an alarm should be fired.
Advantage:
- Policy-based signature algorithms are statistical evaluations of the traffic flow.
- Polices can be used to search for extremely complicated relationships.
Disadvantage:
- Creating a security policy necessitates a thorough understanding of network traffic and is a time-consuming process.
- Only certain sorts of packets can be analyzed using policy-based signature techniques. For example, SYN packets have the SYN bit set during the handshaking process at the start of the session.
- The policy itself may need to be tweaked. You may need to alter the threshold level for particular types of traffic, for example, so that the policy corresponds to the network use patterns it is monitoring.
4.Stateful Protocol Analysis Detection:
- Protocol analysis-based intrusion detection is similar to signature-based intrusion detection, but it performs a more in-depth analysis of the protocols specified in the packets. A deeper analysis examines the payloads within TCP and UDP packets, which contain other protocols. For example, a protocol such as DNS is contained within TCP or UDP, which itself is contained within IP.
- The first step of protocol analysis is to decode the packet IP header information and determine whether the payload contains TCP, UDP, or another protocol. For example, if the payload is TCP, some of the TCP header information within the IP payload is processed before the TCP payload is accessed (for example, DNS data). Similar actions are mapped for other protocols.
- Protocol analysis requires that the IPS sensor knows how various protocols work so that it can more closely analyze the traffic of those protocols to look for suspicious or abnormal activity. For each protocol, the analysis is based not only on protocol standards, particularly the RFCs, but also on how things are implemented in the real world.
The Different Types of IPS and IDS:
There are two types of Intrusion Detection Systems:
Network Intrusion Detection Systems (NIDS): The system is part of the network infrastructure and monitors packets as they flow through the network. NIDS usually co-resides with devices that have span, tap, or mirroring capability, such as switches.
Host-Based Intrusion Detection Systems (HIDS): This software resides on the client, computer, or server devices, and monitors events and files on the device.
There are multiple types of Intrusion Protection Systems:
Network-based Intrusion Prevention System (NIPS): This system is deployed inline in the network infrastructure and examines all traffic in the entire network.
Wireless Intrusion Prevention System (WIPS): This system is part of the wireless network infrastructure and examines all wireless traffic.
Host-based Intrusion Prevention System (HIPS): This software resides on the client, computer, or server devices, and monitors events and files on the device.
Behavior IPS: This system is part of the network infrastructure and examines all traffic for unusual patterns and behavior in the entire network.
Also Read: How to Enable Packet Filtering With Open Source Iptables Firewall/Linux Firewall?
Passive versus Inline mode:
A sensor can be deployed either in Passive mode or inline mode. In Passive mode, the sensor receives a copy of the data for analysis, while the original traffic still makes its way to its ultimate destination. By contrast, a sensor working inline analyzes the traffic live and therefore can actively block the packets before they reach their destination. Some IPS devices can work either in passive mode or inline mode. For example, Cisco ASA AIP SSM. IPS can be kept in the inline mode which will act as both IDS & IPS which is called as Intrusion Detection & Prevention System (IDPR).
- The Benefits and Drawbacks of Using Passive Mode to Deploy an IDS:
| Benefits | Drawbacks |
| Deploying the IDS sensor does not have any impact on the network. | IDS sensor response actions cannot stop the trigger packet and are not guaranteed to stop a connection. IDS response actions are typically better at stopping an attacker more than a specific attack itself. |
| The IDS sensor is not inline and, therefore, a sensor failure cannot affect network functionality. | IDS sensor response actions are less helpful in stopping email viruses and automated attackers such as worms. |
| Overrunning the IDS sensor with data does not affect network traffic; however, it does affect the capability of the IDS to analyze the data. | Users deploying IDS sensor response actions must have a well-thought-out security policy combined with a good operational understanding of their IDS deployments. Users must spend time to correctly tune IDS sensors to achieve expected levels of intrusion detection. |
| Being out of band (OOB), IDS sensors are more vulnerable to network evasion techniques, which are the process of totally concealing an attack. |
2. The Benefits and Drawbacks of Using Inline Mode to Deploy an IPS:
| Benefits | Drawbacks |
| You can configure an IPS sensor to perform a packet drop that can stop the trigger packet, the packets in a connection, or packets from a source IP address. | An IPS sensor must be inline and, therefore, IPS sensor errors or failure can have a negative effect on network traffic. Overrunning IPS sensor capabilities with too much traffic does negatively affect the performance of the network. |
| Being inline, an IPS sensor can use stream normalization techniques to reduce or eliminate many of the network evasion capabilities that exist. | Users deploying IPS sensor response actions must have a well-thought-out security policy combined with a good operational understanding of their IPS deployments. |
| An IPS sensor will affect network timing because of latency, jitter, and so on. An IPS sensor must be appropriately sized and implemented so that time-sensitive applications, such as VoIP, are not negatively affected. |
IPS actions:
The action specifies how the IPS responds to a threat event. Every threat or virus signature that is defined by IPS includes a default action.
- PaloAlto actions list:
When an IPS sensor detects malicious activity, it can choose from any or all the following actions:
- Default: Takes the default action that is specified internally for each threat signature. For antivirus profiles, it takes the default action for the virus signature.
- Allow: Permits the application traffic. The allow action does not generate logs related to the signatures or profiles.
- Alert: Generates an alert for each application traffic flow. The alert is saved in the threat log. Generates an alert when attack volume (cps) reaches the Alarm threshold set in the profile.
- Drop: Drops the application traffic.
- Reset Client: For TCP, resets the client-side connection. For UDP, the connection is dropped.
- Reset Server: For TCP, resets the server-side connection. For UDP, the connection is dropped.
- Reset Both: For TCP, resets the connection on both client and server ends. For UDP, the connection is dropped.
- Block IP: Blocks traffic from either a source or a source-destination pair; Configurable for a specified time.
- Sinkhole: This action directs DNS queries for malicious domains to a sinkhole IP address.
- Random Early Drop: This Causes the firewall to randomly drop packets when connections per second reach the Activate Rate threshold in a DoS Protection profile applied to a DoS Protection rule.
- SYN Cookies: This Causes the firewall to generate SYN cookies to authenticate an SYN from a client when connections per second reach the Activate Rate Threshold in a DoS Protection profile applied to a DoS Protection rule.
2. Cisco Actions list:
When an IPS sensor detects malicious activity, it can choose from any or all the following actions:
- Deny attacker inline: This action terminates the current packet and future packets from this attacker address for a specified time. The sensor maintains a list of the attackers currently being denied by the system. You can remove entries from the list or wait for the timer to expire. The timer is a sliding timer for each entry. Therefore, if attacker A is currently being denied, but issues another attack, the timer for attacker A is reset, and attacker A remains on the denied attacker list until the timer expires. If the denied attacker list is at capacity and cannot add a new entry, the packet is still denied.
- Deny connection inline: This action terminates the current packet and future packets on this TCP flow. This is also referred to as deny flow.
- Deny packet inline: This action terminates the packet.
- Log attacker packets: This action starts IP logging on packets that contain the attacker’s address and sends an alert. This action causes an alert to be written to the event store, which is local to the IOS router, even if the produce-alert action is not selected. Produce alert is discussed later in a bullet.
- Log pair packets: This action starts IP logging on packets that contain the attacker and victim address pair. This action causes an alert to be written to the event store, even if the produce-alert action is not selected.
- Log victim packets: This action starts IP logging on packets that contain the victim address and sends an alert. This action causes an alert to be written to the event store, even if the produce-alert action is not selected.
- Produce alert: This action writes the event to the event store as an alert.
- Produce verbose alert: This action includes an encoded dump of the offending packet in the alert. This action causes an alert to be written to the event store, even if the produce-alert action is not selected.
- Request block connection: This action sends a request to a blocking device to block this connection.
- Request block host: This action sends a request to a blocking device to block this attacker host.
- Request SNMP trap: This action sends a request to the notification application component of the sensor to perform a Simple Network Management Protocol (SNMP) notification. This action causes an alert to be written to the event store, even if the produce-alert action is not selected.
- Reset TCP connection: This action sends TCP resets to hijack and terminate the TCP flow.
Where does the IDPS fit into our security strategy?
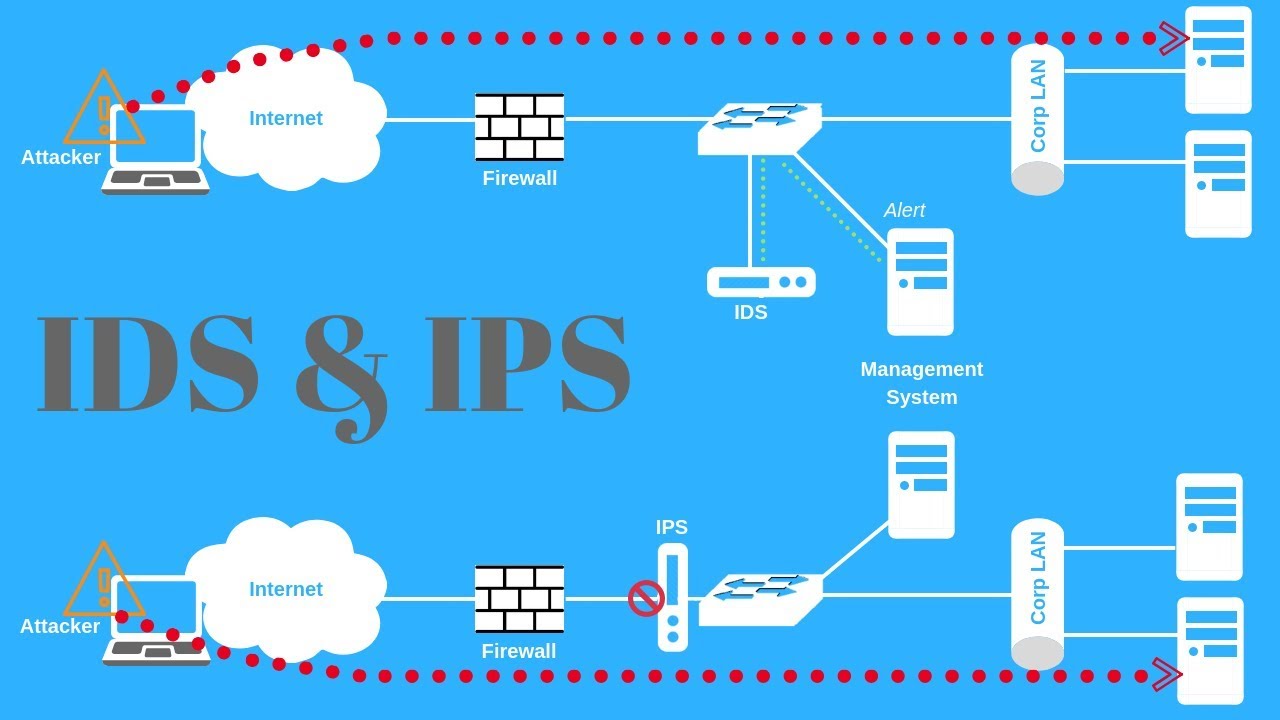
- Our network’s edge or front-end firewall is the first line of protection against attackers, and it will almost certainly have its intrusion detection capacity, however, it will likely only detect and prevent a small number of known attacks/intrusions.
- The organization will be always confused about whether the IPS/IDS should be kept after or before the firewall. Sometimes, the IDS/IPS will be placed after the firewall, so only legitimate traffic will be inspected which will further reduce the load on IDS as well. However, to prevent the firewall from attacks, IPS is installed in front of the firewall.
- One can make an argument either way in certain use cases. But, generally accepted practice is to put an IDS/IPS after the firewall (from the point of view of incoming traffic – i.e. closer to the interior or private network).
- Firewalls are generally designed to be on the network perimeter and can handle dropping a lot of the non-legitimate traffic (attacks, scans, etc.) very quickly at the ingress interface, often in hardware.
- An IDS/IPS is doing more deep packet inspections and that is a much more computationally expensive undertaking. For that reason, we prefer to filter what gets to it with the firewall line of defense before engaging the IDS/IPS to analyze the traffic flow.
- In an even more protected environment, we would also put the first line of defense in ACLs on an edge router between the firewall and the public network(s).
- The IPS sits directly in the communication path between the source and the destination, it analyzes traffic and takes actions like sending alerts, dropping malicious packets, blocking traffic, and resetting connections. Because of this IPS can degrade our network performance if it hasn’t been configured correctly. Our IPS will generally be placed at an edge of the network, such as immediately after a firewall/router, or in front of a server farm. Position the IPS where it will see the bare minimum of traffic it needs to, to keep performance issues under tight control.
- The IDS is a passive system that scans internal network traffic and reports back about potential threats. The most obvious location is at the network perimeter, just inside the firewall.
IDS monitors all network packets right from OSI Layer 2 (Data) to Layer 7 (Application), and stores this vast amount of information in its database.
An IPS monitors traffic at Layer 3 (Network) and Layer 4 (Transport) to ensure that their headers, states, and so on are those specified in the protocol suite.
Why does SOC need IDS/IPS?
SOC analyst work is to analyze the alerts which we used to get from IDS/IPS to keep the environment safe. To know attacks and to dig them more, the IDS and IPS logs are more important. Since it catches the alerts based on the signature, it is very important to implement an Intrusion system in the organization.
IDS freeware:
There are many IDS solutions on the market today, as well as free/open-source IDS tools that you can download. The best solution for our organization depends on our network’s size, security needs, existing security infrastructure, budget and IT department structure, and workload.
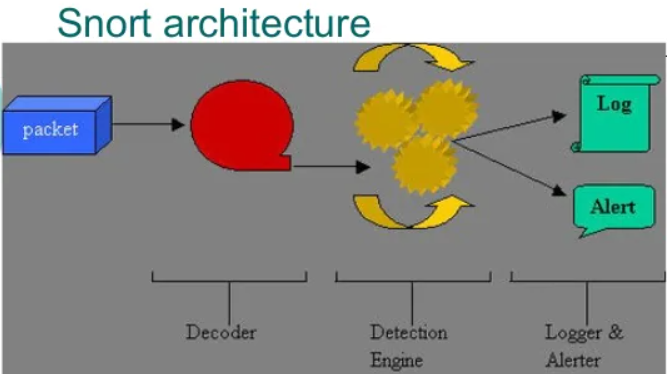
One of the most popular freeware or open-source IDS products is SNORT:
- Snort is an open-source network intrusion prevention and detection system.
- It uses a rule-based language combining signature, protocol, and anomaly inspection methods.
- Snort does real-time analysis of IP packets and can search content and perform pattern matching to detect common attacks such as buffer overflows, SMB probes, port scans, and CGI attacks. There are versions available for both Linux and Windows. There are plug-ins available that extend its detection and reporting capabilities.
- Snort is often thought of as a protocol analyzer, and the line between such “sniffers” and IDS can be thin. Other protocol analyzers and monitors, such as Sunbelt Software’s LanHound, can also perform some IDS functions.
Snort Rule:
Rules are created by known intrusion signatures. These are usually present in snort.conf configuration file.
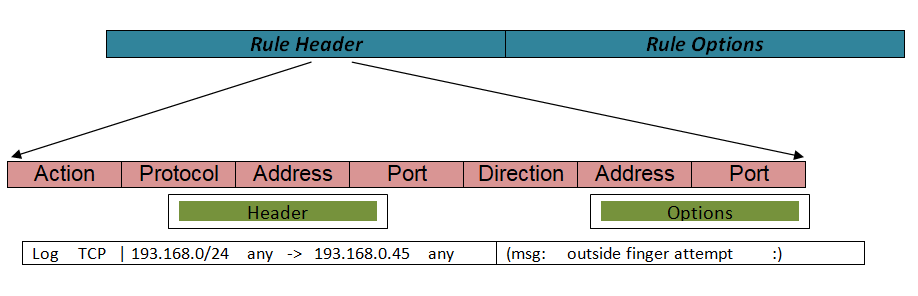
Here,
- “Log” is an action.
- “TCP” is a protocol.
- “193.168.0/24” is the source IP address.
- “any” is the source port.
- “193.168.0.45” is Destination IP.
- “any” is Destination port.
- “msg” is an option keyword.
- “outside finger attempt” is an option argument.
- “:” is an options separator.
Signature explanation:
Rule Name: POLICY DNS Query to DynDNS Domain *.ddns .net
Description: This rule will alert a DNS query to a NOIP Dynamic DNS domain, sometimes used by malware and other unwanted services.
Raw Rule:
alert udp $HOME_NET any -> any 53 (msg:”ET POLICY DNS Query to DynDNS Domain *.ddns .net”; content:”|01|”; offset:2; depth:1; content:”|00 01 00 00 00 00 00|”; distance:1; within:7; content:”|04|ddns|03|net|00|”; nocase; distance:0; fast_pattern; reference:url,www.noip.com/support/faq/free-dynamic-dns-domains; classtype:bad-unknown; sid:2028675; rev:2; metadata:affected_product Any, attack_target Client_Endpoint, created_at 2019_10_11, deployment Perimeter, former_category POLICY, performance_impact Low, signature_severity Informational, updated_at 2019_10_11;)
Formatted log:
Action: alert
Network Match: alert udp $HOME_NET any -> any 53
Here,
- “Log” is an alert.
- “UDP” is a protocol.
- ” HOME_NET” is the source IP address.
- “any” is the source port.
- “any” is Destination IP.
- “53” is Destination port.
Here the alert will be triggered if any UDP query is initiated from a home network and from any port towards any IP and if the destination port is 53.
Msg: ET POLICY DNS Query to DynDNS Domain *.ddns .net
SID: 2028675
Rule Body:
reference: url,www.noip.com/support/faq/free-dynamic-dns-domains; within: 7; fast_pattern; nocase; offset: 2; content: |01|; content: |00 01 00 00 00 00 00|; content: |04|ddns|03|net|00|; metadata: affected_product Any, attack_target Client_Endpoint, created_at 2019_10_11, deployment Perimeter, former_category POLICY, performance_impact Low, signature_severity Informational, updated_at 2019_10_11; depth: 1; distance: 1; distance: 0;
Conclusion:
You can level the playing field against threat actors and their attack tactics by using a layered security solution that combines signature and behavior-based technologies with other tools. Keep in mind that internet security risks are getting more stealthy and severe. The Intrusion Detection & Prevention System’s integrated capabilities, whether network or host-based, is one tool worthy of consideration.