Proxyware platforms enable users to sell the use of their unused internet bandwidth, typically by running a client application. The client application is responsible for joining their system to a network that is operated by the platform provider.
Proxyware programs that share a part of the Internet bandwidth that is currently available on a system to others. Users who install the program are usually paid with a certain amount of cash in exchange for providing the bandwidth. Companies that provide such a service include Peer2Profit and IPRoyal.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
While users can earn some money from installing proxyware on their systems, they should know they are taking risks by allowing external users to perform certain behaviors by using their networks. For instance, users cannot know in detail the companies that the proxyware platforms claim to use their services. Even if they can verify their customers on their own, it is impossible to check if your bandwidth will be maliciously exploited in the future or not.
The ASEC analysis team recently discovered malware strains installing proxyware without the user’s permission. Users whose systems are infected with the malware have their network bandwidth stolen by attackers to gain profit. The method of earning profit by using the infected system’s resources is similar to that of CoinMiner.
Also Read: Hunting for Suspicious Windows Services – Mind Map
1. Case using Adware
The post will first discuss malware distributed through adware. AhnLab’s ASD log shows that the proxyware is installed through adware such as Neoreklami.
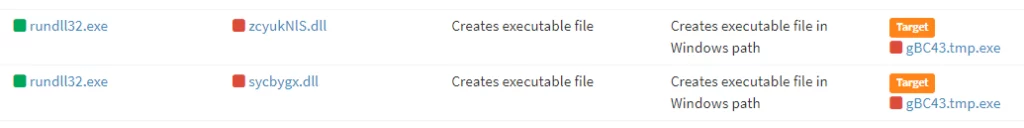
It is a dropper-type malware that installs proxyware of Peer2Profit and IPROYAL on the system as a user account without the user’s permission.
2. Cases of attacks targeting vulnerable MS-SQL servers
Peer2Profit is used by other attackers as well. The log of Peer2Profit SDK being installed on a vulnerable MS-SQL server. The system also has infection logs of various malware strains distributed through the dictionary attack such as CoinMiner and backdoor. It is likely that the malware installing proxyware was distributed through the dictionary attack as the system had vulnerable account credentials.
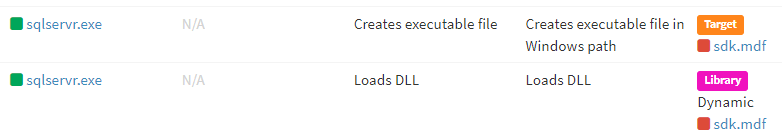
The “sdk.mdf” file is packed with UPX. It has been installed on multiple vulnerable MS-SQL servers starting from early June in 2022.
Also Read: Mapping MITRE ATT&CK with Window Event Log IDs
[IOC]
MD5
Dropper
– 05ed95d997662ee0ba15f76949955bf0
– dd709b8529802d6489311a27372044aa
– 29cbc8a8cdb0e24f3561fac8ac0c0174
Peer2Profit SDK
– b1781c2670a2e0a35a10fb312586beec
– e34d9ec5d43501dc77ee93a4b464d51b
IPRoyal Pawns
– 7f8c85351394fd8221fc84d65b0d8c3e
– 3e4bb392494551a89e090fbe1237f057
Detection & Response:
- Monitor DNS requests for iproyal.com and peer2profit.io
- The malware strains are distributed through adware or installed on vulnerable MS-SQL servers. Users should refrain from installing programs from unknown sources.
- Create hunt queries for the iproyal.exe process running from the location located in %PROGRAMFILES%\IPRoyal Pawns\resources\packages\main\resources\ or Windows any path locations
- Hunt for file name “sdk.mdf” using EDR tools.
- Check for file names such “\IPRoyal” or “peer2profit” as under %PROGRAMFILES%
Source/Credits: https://asec.ahnlab.com/en/37276/